Users
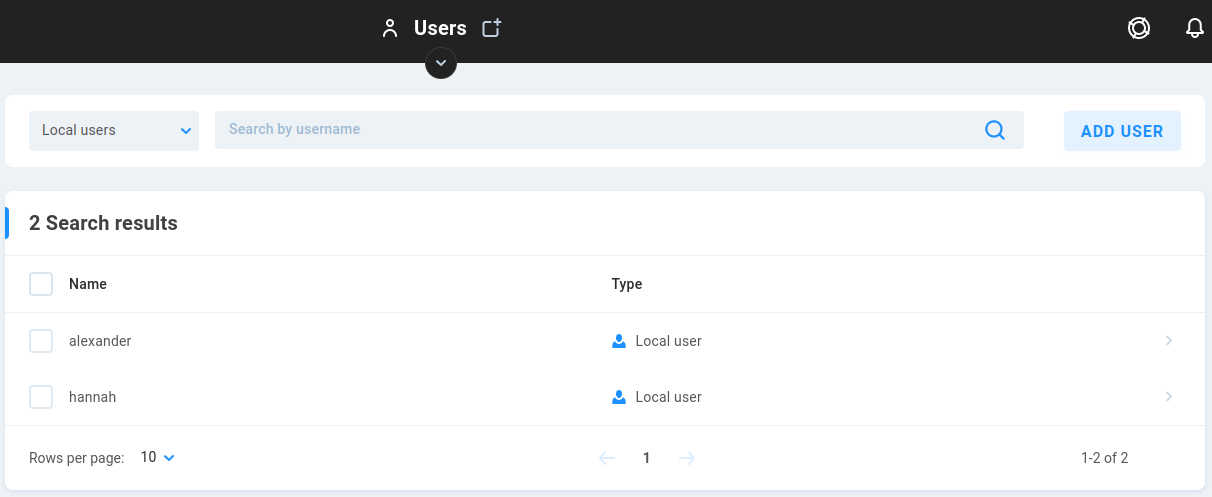
The Users page allows permissions to be created for user access to NAS shares hosted on EVO.
The dropdown menu at the top left allows for view selection for the existing users. The ADD USER button will change to AD/LDAP depending on whether the selection is for local or external user/group.
Once the user/group is created, click on it to assign SMB share access or make modifications.
Local users are users created on EVO.
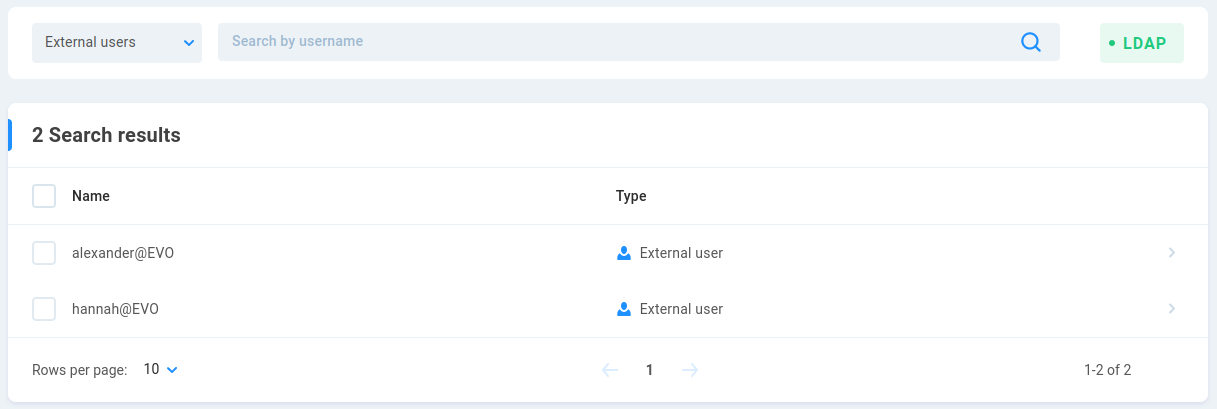
External users are imported from an external user directory service such as Active Directory.
Local groups are EVO administrator-defined groups created for EVO local users. This allows for per-group permissions to be applied to a number of users with a single modification.
External groups are groups imported from an external directory service. This allows for per-group permissions to be applied to a number of users with a single modification.
Search by username - Enter a full or partial search to retrieve any matches. For instance, searching a single letter will return all names that contain that letter.
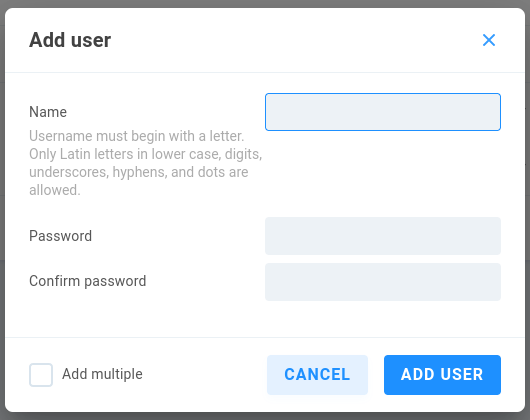
Add User allows for creation of one or multiple EVO local users or groups.
User/group names must begin with a letter. Only Latin letters in lower case, digits, underscores, hyphens, and dots are allowed.
Tip
Assign permissions according to local or external user groups for quicker permission application than per-user modification.
Sync with AD/LDAP
EVO can join to either Active Directory or another LDAP server. Connecting to one will prevent connection to the other. Choose External groups from the drop-down menu on the Users page to expose the AD/LDAP button.
For either directory service, keep the following considerations in mind:
EVO can use either Active Directory or LDAP, but not both simultaneously.
Names of users and groups must contain only Latin letters and digits and must be shorter than 32 characters. Dots, dashes, and underscores are allowed, but names with spaces and other special characters will not be imported.
A conflict with EVO’s internal root user may be created if the directory also has a user named “root”.
EVO must be pointed at a DNS provider that can resolve the directory server’s hostname. This is found at the Connectivity page in the EVO web interface.
The EVO clock must also be in agreement with the directory server’s clock. The EVO time is found at the System page, and the NTP server or NTP client role can be chosen. Check the Connectivity page to ensure a gateway is properly configured if an internet provider is to be used.
When mounting EVO NAS shares in an Active Directory environment, authentication for non-AD EVO users (created in the EVO web administration) will require instruction that the AD domain not be used. Prepending “evo” to the username in the workstation’s mount prompt (example “evo\alexander”) will tell the workstation to use the evo domain, rather than the local domain. If an alternate domain is not specified, the workstation will default to using the Active Directory domain, and EVO will expect an AD user rather than a local one.
Active Directory
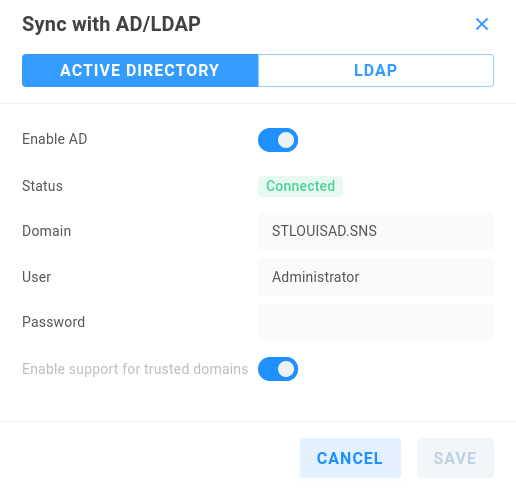
Enable AD toggles the connection to the AD Server on/off.
Status displays current AD connection status.
Domain - Specify the domain name (ensure this is resolvable by DNS).
User - Enter the name of an AD user. By default, any AD user that’s created is a member of the “Domain Users” group, which allows the user to create a computer object for EVO and authorize its connection. If the user account cannot create a computer object for EVO in AD, the computer object and delegate control can be manually added by the AD administrator.
Password - Enter the AD user password.
Enable support for trusted domains - when enabled, allows EVO to join to a child domain that presents objects from parent (requires enabling of the “Global Catalog” option in NTDS Settings Properties on the AD server).
Note
Once connected, searching for a user may require the domain name to be included with their name, especially if multiple domains are available.
LDAP
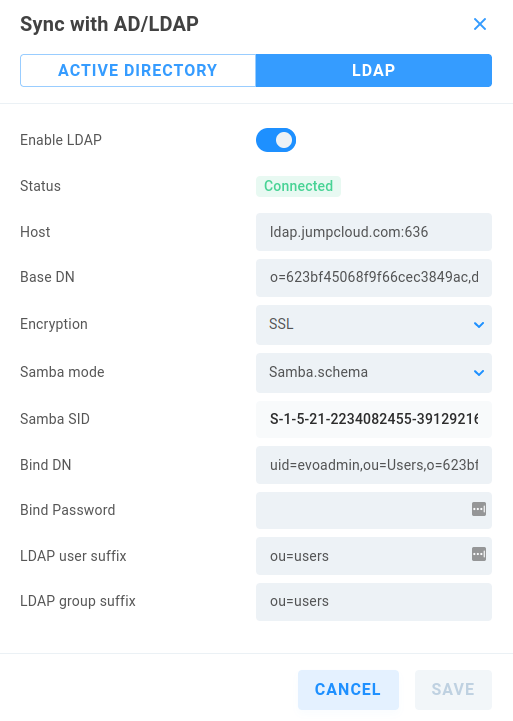
Enable AD toggles the connection to the LDAP Server on/off
Status displays current LDAP connection status
Host - Enter the host name:port for the LDAP server
Base DN - Enter the string provided by the LDAP server (o=%SECRET%,dc=%DOMAINCOMPONENT%,dc=com)
Encryption - Choose None, SSL, or TLS - certificates are imported at the System > Advanced page using the Certificate authority card
Samba mode - Samba.schema is required for SMB authentication
Samba SID - Unique security identifier for EVO (note the string is longer than the field, so ensure it’s all copied when connecting)
Bind DN - Enter the LDAP distinguished name (uid=%BIND DN USER%,ou=Users,o=%SECRET%,dc=%DOMAINCOMPONENT%,dc=com)
Bind Password - %BIND DN USER PASSWORD%
LDAP user suffix - Default is common name “cn=users”
LDAP group suffix - Default is common name “cn=groups”
LDAP certificate authority - Upload the G2 root certificate if required by the LDAP server